Hi guys,
I configured Enterprise User Security with user entries being in AD, and connection between EUS/ Oracle Database been made using OUD proxy using kerberos authentication.
I mainly followed these Oracle Support Documents (https://support.oracle.com):
- EUS AD Integration Using OUD Proxy (Doc ID 1571196.1)
- Configuring ASO Kerberos Authentication with a Microsoft Windows 2008 R2 Active Directory KDC (Doc ID 1304004.1)
However, when I tried to log in to the database I got the following error:
-------------------- 8< --------------------
[oracle@db ~]$ okinit -e 23 rgreen
Kerberos Utilities for Linux: Version 11.2.0.4.0 - Production on 03-JAN-2014 13:58:25
Copyright (c) 1996, 2013 Oracle. All rights reserved.
Password for rgreen@EXAMPLE.COM:
[oracle@db ~]$ sqlplus /@orcl
SQL*Plus: Release 11.2.0.4.0 Production on Fri Jan 3 14:06:22 2014
Copyright (c) 1982, 2013, Oracle. All rights reserved.
ERROR:
ORA-28293: No matched Kerberos Principal found in any user entry
-------------------- 8< --------------------
The OUD access log tells what went wrong:
-------------------- 8< --------------------
[18/Dec/2013:20:56:25 +0100] CONNECT conn=77 from=127.0.0.1:37607 to=127.0.0.1:51636 protocol=LDAPS
[18/Dec/2013:20:56:25 +0100] BIND REQ conn=77 op=0 msgID=1 type=SASL mechanism=DIGEST-MD5 dn="cn=orcl,cn=oraclecontext,dc=example,dc=com"
[18/Dec/2013:20:56:25 +0100] BIND RES conn=77 op=0 msgID=1 result=14 etime=0
[18/Dec/2013:20:56:25 +0100] BIND REQ conn=77 op=1 msgID=2 type=SASL mechanism=DIGEST-MD5 dn="cn=orcl,cn=oraclecontext,dc=example,dc=com"
[18/Dec/2013:20:56:25 +0100] BIND RES conn=77 op=1 msgID=2 result=0 authDN="cn=orcl,cn=OracleContext,dc=example,dc=com" etime=2
[18/Dec/2013:20:56:25 +0100] SEARCH REQ conn=77 op=2 msgID=3 base="cn=OracleDBSecurity,cn=Products,cn=OracleContext,dc=example,dc=com" scope=one filter="(&(objectclass=orcldbenterprisedomain_82)(uniqueMember=cn=orcl,cn=OracleContext,dc=example,dc=com))" attrs="orclDBAuthTypes,dn"
[18/Dec/2013:20:56:25 +0100] SEARCH RES conn=77 op=2 msgID=3 result=0 nentries=1 etime=2
[18/Dec/2013:20:56:25 +0100] SEARCH REQ conn=77 op=3 msgID=4 base="cn=Common,cn=Products,cn=OracleContext,dc=example,dc=com" scope=base filter="(objectclass=*)" attrs="ALL"
[18/Dec/2013:20:56:25 +0100] SEARCH RES conn=77 op=3 msgID=4 result=0 nentries=1 etime=4
[18/Dec/2013:20:56:25 +0100] SEARCH REQ conn=77 op=4 msgID=5 base="cn=Users,dc=example,dc=com" scope=sub filter="(krbPrincipalName=rgreen@EXAMPLE.COM)" attrs="dn"
[18/Dec/2013:20:56:25 +0100] SEARCH PROXY_REQ conn=77 op=4 msgID=5 s_conn=21 scope="sub" s_msgid=34 base="cn=Users,dc=example,dc=com" s_credmode=use-client-identity filter="(krbPrincipalName=rgreen@EXAMPLE.COM)"
[18/Dec/2013:20:56:25 +0100] SEARCH PROXY_RES conn=77 op=4 msgID=5 result=0 s_conn=21 s_msgid=34 etime=1 authzDN=cn=orcl,cn=OracleContext,dc=example,dc=com nentries=0
[18/Dec/2013:20:56:25 +0100] SEARCH RES conn=77 op=4 msgID=5 result=0 nentries=0 etime=1
[18/Dec/2013:20:57:25 +0100] UNBIND REQ conn=77 op=5 msgID=6
[18/Dec/2013:20:57:25 +0100] DISCONNECT conn=77 reason="Client Disconnect"
-------------------- 8< --------------------
So the database searches for krbPrincipalName, but userPrincipalName is the standard attribute in AD.
To fix this the attribute orclCommonKrbPrincipalAttribute in the EUS configuration has to be changed from krbPrincipalName to userPrincipalName. Although this attribute is documented here it took me a while to find it.
To change the value of the krbPrincipalName proceed as follows:
1) Create file ldapmodify.ldif:
dn: cn=Common,cn=Products,cn=OracleContext,dc=example,dc=com
changetype: modify
replace: orclCommonKrbPrincipalAttribute
orclCommonKrbPrincipalAttribute: userPrincipalName
2) Run the ldapmodify command:
ldapmodify -h db.example.com -p 51389 -D "cn=Directory Manager" -j /tmp/password.txt -v -f ldapmodify.ldif
Of course, domain, hostname etc. must be replaced.
Regards,
Roy
Monday, June 2, 2014
Sunday, June 1, 2014
Oracle Audit Vault Server 12.1.2 Installation
Oracle has merged the two Oracle Audit Vault and Oracle Database Firewall into the new Oracle Audit Vault and Database Firewall. Audit Vault and Database Firewall installation comprises of installing Audit Vault first and then Database Firewall. It is possible to use only one part of the product, but you will have to install the Audit Vault Server in any case as this is also the repository for the Database Firewall. This post deals with Audit Vault Server installation only.
For more information about the product click here and for the official product documentation click here.
- Download Software from Oracle Software Delivery Cloud:
https://edelivery.oracle.com/ - Search required media
- In Product Pack select Oracle Database
- In Platform select Linux x86-64
- Download Media
- Hardware Requirements
- 2 GB of RAM
- A single hard drive with a minimum 125 GB of disk space
- At least 1 Network Interface Card
- Installation
- Boot the ISO image avs-installer-disc-12.1.2.0.0.iso
Type install if you wish to skip a memory test
- Sit back, have a coffee or tea and watch the Audit Vault Server being installed...
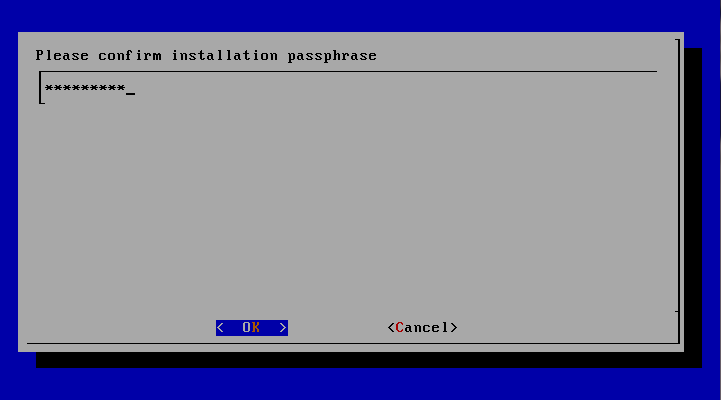
- Enter Installation Passphrase (and confirm)
- Network Configuration
- Once the network configuration is complete the server will rebootThe first boot will take a long time
- Installation Complete
- Post Installation
- To access the Audit Vault Server Post-Configuration page, open any internet browser and enter the ip address of the Audit Vault Server, in my case https://192.168.56.31 (see Network Configuration)
- Click Proceed anyway (or similar). This is due to self-signed certificate.
- Enter Installation Passphrase that you created during the installation
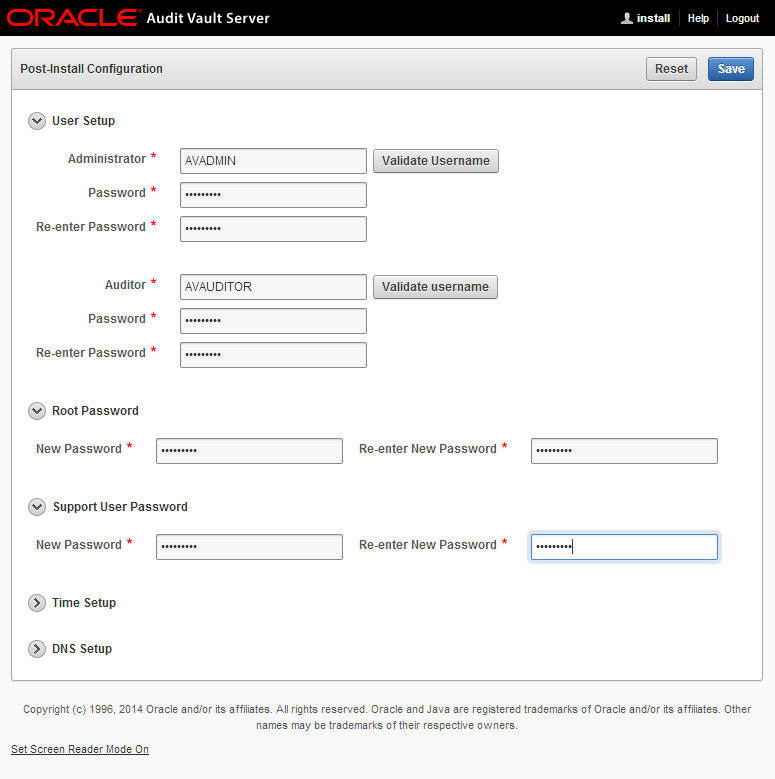
- Set up usernames and passwords
- First login
That's it really. As you could see the installation isn't really more than specifying the IP address and passwords.
Subscribe to:
Comments (Atom)